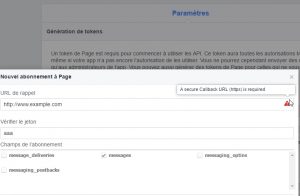
If you want to try the new facebook bot capability you could come across the need of an HTTPS webserver for the callback URL:
Anyway….since https is becoming the standard (http://trends.builtwith.com/ssl/SSL-by-Default, https://security.googleblog.com/2014/08/https-as-ranking-signal_6.html) it could be interesting to learn more about it and give it a try…
Want to know more about https? Google!
Next step… you need a certificate. It needs to be provided by a certificate authority and it will cost you some money (depending on the authority and certificate type but once again…..google). You could buy one on rapidSSL for hundred dollars (https://www.rapidssl.com/) but since few weeks there is a new player in town provided free certificates: let’s encrypt.
“Let’s Encrypt is a free, automated, and open certificate authority (CA), run for the public’s benefit. Let’s Encrypt is a service provided by the Internet Security Research Group (ISRG).”
The service went out of beta in April 2016 with some limitation but the initiative is promising so I decided to try it.
The documentation is pretty good :
First you retrieved the client with
wget https://dl.eff.org/certbot-auto chmod a+x ./certbot-auto
then you check the options
$ ./certbot-auto --help Usage: certbot-auto [OPTIONS] A self-updating wrapper script for the Certbot ACME client. When run, updates to both this script and certbot will be downloaded and installed. After ensuring you have the latest versions installed, certbot will be invoked with all arguments you have provided. Help for certbot itself cannot be provided until it is installed. --debug attempt experimental installation -h, --help print this help -n, --non-interactive, --noninteractive run without asking for user input --no-self-upgrade do not download updates --os-packages-only install OS dependencies and exit -v, --verbose provide more output
You need to find the plugin to use depending on your webserver (more info HERE). I used the standalone plugin since there is nothing for nodejs. With this plugin the client will use the port 443 to act as a webserver to handle some challenge to prove that its own the domain.
./certbot-auto certonly --standalone --email charles.walker.37@gmail.com -ddjynet.xyz
The output will give you information about where the certificat/key have been generated so you can use them :
Congratulations! Your certificate and chain have been saved at /etc/letsencrypt/live/djynet.xyz/fullchain.pem......
Then we can try it with a simple page served by nodejs.
Here is a very simple https nodejs server (from the official doc : https://nodejs.org/api/https.html)
var fs = require('fs');
var https = require('https');
var options = {
key: fs.readFileSync('/etc/letsencrypt/live/djynet.xyz/privkey.pem'),
cert: fs.readFileSync('/etc/letsencrypt/live/djynet.xyz/cert.pem')
};
https.createServer(options, function (req, res) {
console.log(new Date()+' '+
req.connection.remoteAddress+' '+
req.method+' '+req.url);
res.writeHead(200);
res.end("hello world\n");
}).listen(443,"0.0.0.0");
Let’s run it with
$ sudo node main.js Fri Jun 03 2016 02:41:57 GMT+0000 (UTC) 73.68.66.138 GET / Fri Jun 03 2016 02:41:57 GMT+0000 (UTC) 73.68.66.138 GET /favicon.ico
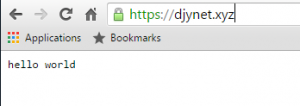
And check the result
Nice green lock… we’re safe !
Warning!
I discover few days after that it was node 100% working. The nodejs server does not provide the chain of certificate. See my follow up article to fix it HERE.

Pingback: Let’s encrypt TLS setup for nodejs | Djynet
Pingback: Let’s encrypt with docker | Djynet